Code:
http://blog.threatexpert.com/2008/10/gimmiva-exploits-zero-day-vulnerability.html
.....
The most interesting part of this worm is implemented in the DLL basesvc.dll. This DLL is responsible for the network propagation of the worm.
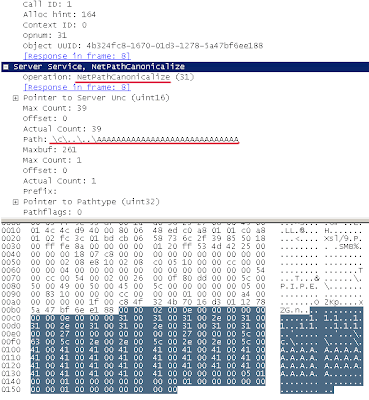
It starts from probing other IPs from the same network by sending them a sequence of bytes "abcde" or "12345". The worm then attempts to exploit other machines by sending them a malformed RPC request and relying on a vulnerable Server service. As known, Server service uses a named pipe SRVSVC as its RPC interface, which is registered with UUID equal to 4b324fc8-1670-01d3-1278-5a47bf6ee188. In order to attack it, the worm firstly attempts to bind SRVSVC by constructing the following RPC request:
Next, Gimmiv.A submits a maliciously crafted RPC request that instructs SRVSVC to canonicalize a path "\c\..\..\AAAAAAAAAAAAAAAAAAAAAAAAAAAAA" by calling the vulnerable RPC request NetPathCanonicalize, as shown in the traffic dump below (thanks to Don Jackson from SecureWorks for the provided dump):

Cách khắc phục theo em là diệt ngay nó, hiện tại đã có vài AV detect được nó, và nhanh chóng cập nhật bản vá.![[digg] [digg]](/hvaonline/templates/viet/images/digg.gif)
![[delicious] [delicious]](/hvaonline/templates/viet/images/delicious.gif)
![[google] [google]](/hvaonline/templates/viet/images/google.gif)
![[yahoo] [yahoo]](/hvaonline/templates/viet/images/yahoo.gif)
![[technorati] [technorati]](/hvaonline/templates/viet/images/technorati.gif)
![[reddit] [reddit]](/hvaonline/templates/viet/images/reddit.gif)
![[stumbleupon] [stumbleupon]](/hvaonline/templates/viet/images/stumbleupon.gif)



![[Minus] [Minus]](/hvaonline/templates/viet/images/minus.gif)
![[Plus] [Plus]](/hvaonline/templates/viet/images/plus.gif)