Chào các bạn và các anh chị em
Mình đã cài 5 lần 7 lượt snort theo các hướng dẫn tiếng việc và tiếng anh nhưng đều không hoạt động, qua 1 số lần có kinh nghiệm mình đã làm gần được rồi, mặc dù vấn đề các lỗi thường gặp khi triển khai snort mình đã tham khảo qua hết tất các các bài viết trên này và trên 4rum nhatnghe, nhưng vẫn còn 2 vần đề trục trặc sau mà mình muốn hỏi.
Trước tiên Mình xin trình bày toàn bộ quá trình cài đặt snort của mình để mọi người tiện quan sát và xem thử có chỗ nào sai.
Mô hình của mình là làm trên máy ảo VmWare, 1 máy ảo CentOS 6.4 i386 em dùng để triển khai Snort, mình dùng bản snort-2.9.5.5, 1 máy Windows XP dùng để test hoạt động của Snort. Lớp mạng mình dùng là 192.168.1.0/24 (máy CentOS có IP 192.168.1.2, máy Win XP có IP 192.168.1.3) Sau khi tiến hành cài các gói phần mềm cần thiết cho việc cài Snort thì mình tiến hành cài Snort theo hướng dẫn của trang snort.org như sau:
Các file cài đặt và file rule của snort em để trong /usr/local/src/
Code:
cd /usr/local/src
tar -xzvf snort-2.9.5.5.tar.gz
cd snort-2.9.5.5
Chỗ này mình tham khảo trên mạng nói là các bản snort 2.9.x.x trở lên không nên chạy với –with-mysql ngay từ đầu vì chắc chắn sẽ có lỗi mà chỉ chạy với --with-sourcefire
Code:
./configure --enable-sourcefire
make
make install
Tạo thư mục làm việc của snort là /etc/snort
Code:
cd /etc
mkdir –p snort
cd snort
Chép hết các file trong snort-2.9.5.5/etc vừa giải nén được và vào /etc/snort
Code:
cp /usr/local/src/snort-2.9.5.5/etc/* .
Bước giải nén và chép các rules
Code:
tar -xzvf /usr/local/src/snortrules-snapshot-2955.tar.gz
cp ./etc/* .
touch /etc/snort/rules/white_list.rules
touch /etc/snort/rules/black_list.rules
mkdir /var/log/snort
Tạo nhóm người dùng và user
Code:
groupadd -g 40000 snort
useradd -g snort snort
chown -R snort:snort *
chown -R snort:snort /var/log/snort
Sửa file cấu hình snort.conf các dòng sau
Code:
Code:
ipvar HOME_NET 192.168.1.0/24
ipvar EXTERNAL_NET !$HOME_NET
var RULE_PATH /etc/snort/rules
var SO_RULE_PATH /etc/snort/so_rules
var PREPROC_RULE_PATH /etc/snort/preproc_rules
var WHITE_LIST_PATH /etc/snort/rules
var BLACK_LIST_PATH /etc/snort/rules
output unified2: filename snort.log, limit 128
Code:
cd /usr/local/src
chown -R snort:snort daq-2.0.1
chmod -R 755 daq-2.0.1
chown -R snort:snort snort-2.9.5.5
chmod -R 755 snort-2.9.5.5
chown -R snort:snort snort_dynamicsrc
chmod -R 700 snort_dynamicsrc
Thiết lập snort khởi động cùng hệ thống
Code:
cd /usr/local/src/snort-2.9.5.5
cd rpm
cp snortd /etc/init.d
chkconfig --add snortd
ln -s /usr/local/bin/snort snort
cd /usr/local/src/snort-2.9.5.5/rpm/
cp snort.sysconfig /etc/sysconfig/snort
chmod 755 /etc/init.d/snortd
chmod 755 /etc/sysconfig/snort
chmod 755 /var/log/snort
cd /usr/local/lib
chown -R snort:snort snort*
chown -R snort:snort snort_dynamic*
chown -R snort:snort pkgconfig
chmod -R 755 snort*
cd /usr/local/bin
chown -R snort:snort daq-modules-config
chown -R snort:snort u2*
chmod -R 755 daq-modules-config
chmod 755 u2*
chown -R snort:snort snort
chmod -R 755 snort
Kiểm tra hoạt động của snort bằng 1 trong 2 dòng lệnh đưới đây
Code:
./snort -T -i eth0 -u snort -g snort -c /etc/snort/snort.conf
./snort -A fast -b -d -D -i eth0 -u snort -g snort -c /etc/snort/snort.conf -l /var/log/snort
Thấy hiển thị
Code:
snort 28765 0.3 28.7 400772 146936 ? Ssl 02:36 0:00 ./snort -A fast -b -d -D -i eth0 -u snort -g snort -c
/etc/snort/snort.conf -l /var/log/snort
root 28854 0.0 0.1 4356 752 pts/0 S+ 02:39 0:00 grep -i snort
Code:
Thấy hiển thị
Code:
Stopping snort: [ OK ]
Starting snort: Spawning daemon child...
My daemon child 3090 lives...
Daemon parent exiting (0)
[ OK ]
Code:
Thấy hiển thị
Code:
snort (pid 1886) is running...
Đến bước cài barnyard2-1.9
Code:
cd /usr/local/src
wget http://pear.php.net/go-pear.phar
php go-pear.phar
pear install Image_Graph-alpha Image_Canvas-alpha Image_Color Numbers_Roman
tar -xzvf barnyard2-1.9.tar.gz
cd barnyard2-1.9
./configure --with-mysql
make
make install
Copy file cấu hình barnyard2 vào /etc/snort
Code:
cp etc/barnyard2.conf /etc/snort/
cp schemas/create_mysql /usr/local/src
Sửa file cấu hình barnyard các dòng sau
Code:
vi /etc/snort/barnyard2.conf
Code:
config reference_file: /etc/snort/reference.config
config classification_file: /etc/snort/classification.config
config gen_file: /etc/snort/gen-msg.map
config sid_file: /etc/snort/sid-msg.map
config hostname: localhost
config interface: eth0
output alert_fast: stdout
output database: log, mysql, user=snort password=123456
output database: alert, mysql, user=snort password=123456 dbname=snort host=localhost
Thiết lập barnyard khởi động cùng hệ thống
Code:
cp rpm/barnyard2 /etc/init.d
chmod +x /etc/init.d/barnyard2
cp rpm/barnyard2.config /etc/sysconfig/barnyard2
chkconfig --add barnyard2
ln -s /usr/local/etc/barnyard2.conf /etc/snort/barnyard.conf
ln -s /usr/local/bin/barnyard2 /usr/bin/
mkdir /var/log/barnyard2
chmod 755 /var/log/barnyard2
touch /var/log/snort/barnyard2.waldo
chown snort.snort /var/log/snort/barnyard2.waldo
cd /etc/init.d
chkconfig barnyard2 on
Ở bước này và các bước sau khi cài xong adodb, base hay tạo CSDL thì Code:
service barnyard2 restart
bị lỗi sau:
Code:
Shutting down Snort Output Processor (barnyard2): [FAILED]
Starting Snort Output Processor (barnyard2): [ OK ]
Kiểm tra thêm bằng lệnh
Code:
Thấy hiện thị
Code:
barnyard2 dead but subsys locked
Bước tạo CSDL cho snort
Code:
mysqladmin -u root password 123456
mysql -u root –p
Enter password: 123456
mysql> use mysql;
mysql> CREATE USER 'snort'@'localhost' IDENTIFIED BY '123456';
mysql> create database snort;
mysql> grant create, insert, select, delete, update on snort.* to snort@localhost;
mysql> set password for snort@localhost=PASSWORD('123456');
mysql> flush privileges;
mysql> exit;
mysql -p
Enter password:
mysql> show databases;
+--------------------+
| Database |
+--------------------+
| information_schema|
| mysql |
| snort |
| test |
+--------------------+
Tạo bảng cho snort, Ở bước tạo table này mình không làm theo các cách như trên mạng hay như trong 1 số hướng dẫn như
Code:
mysql –u root –p –D snort < /usr/local/src/snort-2.9.5.5/schemas/create_mysql
hay
mysql –u root –p –D snort < /usr/local/src/barnyard2-1.9/schemas/create_mysql
vì thấy các file create_mysql trong các đường dẫn trên có sẵn rồi và cũng có thử cả 2 câu lệnh trên thấy nó báo mysql [-OPTION] [--help] gì đó và không tạo được, thấy trên mạng có 1 cách như dưới và mình làm thử thì đã tạo được bảng.
Code:
mysql> use snort;
mysql> source /usr/local/src/create_mysql
mysql> show tables;
+------------------+
| Tables_in_snort |
+------------------+
| data |
| detail |
| encoding |
| event |
| icmphdr |
| iphdr |
| opt |
| reference |
| reference_system|
| schema |
| sensor |
| sig_class |
| sig_reference |
| signature |
| tcphdr |
| udphdr |
+------------------+
Bước cài base và adodb
Code:
cd /var/www/html
tar -xzvf adodb511.tgz
tar -xzvf base-1.4.5.tar.gz
mv base-1.4.5/ base/
cd base
cp base_conf.php.dist base_conf.php
Code:
Sửa các dòng sau
Code:
$BASE_urlpath = '/base';
$DBlib_path = '/var/www/html/adodb5';
$DBtype = 'mysql';
$alert_dbname = 'snort';
$alert_host = 'localhost';
$alert_user = 'snort';
$alert_password = '123456';
$archive_exists = 1;
$archive_dbname = 'snort';
$archive_host = 'localhost';
$archive_user = 'snort';
$archive_password = '123456';
chmod 777 /var/www/html/base
Code:
vi /etc/sysconfig/barnyard2
sửa dòng
Code:
Trong quá trình khắc phục 1 số lỗi thì mình đã có chỉnh sửa 1 số file sau nên mình show hết ra lại cho anh em xem xét.
Code:
vi /etc/sysconfig/barnyard2
Code:
# Config file for /etc/init.d/barnyard2
LOG_FILE="snort.log"
# You probably don't want to change this, but in case you do
SNORTDIR="/var/log/snort"
INTERFACES="eth0"
# Probably not this either
CONF=/etc/snort/barnyard.conf
EXTRA_ARGS=""
Code:
Code:
!/bin/sh
#
# Init file for Barnyard2
#
# chkconfig: 2345 40 60
# description: Barnyard2 is an output processor for snort.
#
# processname: barnyard2
# config: /etc/sysconfig/barnyard2
# config: /etc/snort/barnyard.conf
# pidfile: /var/lock/subsys/barnyard2.pid
source /etc/rc.d/init.d/functions
source /etc/sysconfig/network
### Check that networking is up.
[ "${NETWORKING}" == "no" ] && exit 0
[ -x /usr/sbin/snort ] || exit 1
[ -r /etc/snort/snort.conf ] || exit 1
### Default variables
SYSCONFIG="/etc/sysconfig/barnyard2"
### Read configuration
[ -r "$SYSCONFIG" ] && source "$SYSCONFIG"
RETVAL=0
prog="barnyard2"
desc="Snort Output Processor"
start() {
echo -n $"Starting $desc ($prog): "
for INT in $INTERFACES; do
PIDFILE="/var/lock/subsys/barnyard2-$INT.pid"
ARCHIVEDIR="$SNORTDIR/$INT/archive"
WALDO_FILE="$SNORTDIR/$INT/barnyard2.waldo"
BARNYARD_OPTS="-D -c $CONF -d $SNORTDIR/${INT} -w $WALDO_FILE -f $SNORTDIR/${INT} -a $ARCHIVEDIR -f $LOG_FILE -X $PIDFILE $EXTRA_ARGS"
daemon $prog $BARNYARD_OPTS
done
RETVAL=$?
echo
[ $RETVAL -eq 0 ] && touch /var/lock/subsys/$prog
return $RETVAL
}
stop() {
echo -n $"Shutting down $desc ($prog): "
killproc $prog
RETVAL=$?
echo
[ $RETVAL -eq 0 ] && rm -f /var/lock/subsys/$prog
return $RETVAL
}
restart() {
stop
start
}
reload() {
echo -n $"Reloading $desc ($prog): "
killproc $prog -HUP
RETVAL=$?
echo
return $RETVAL
}
case "$1" in
start)
start
;;
stop)
stop
;;
restart)
restart
;;
reload)
reload
;;
condrestart)
[ -e /var/lock/subsys/$prog ] && restart
RETVAL=$?
;;
status)
status $prog
RETVAL=$?
;;
dump)
dump
;;
*)
echo $"Usage: $0 {start|stop|restart|reload|condrestart|status|dump}"
RETVAL=1
esac
exit $RETVAL
Code:
Code:
#!/bin/sh
# $Id$
#
# snortd Start/Stop the snort IDS daemon.
#
# chkconfig: 2345 40 60
# description: snort is a lightweight network intrusion detection tool that \
# currently detects more than 1100 host and network \
# vulnerabilities, portscans, backdoors, and more.
#
# Source function library.
. /etc/rc.d/init.d/functions
# Source the local configuration file
. /etc/sysconfig/snort
# Convert the /etc/sysconfig/snort settings to something snort can
# use on the startup line.
if [ "$ALERTMODE"X = "X" ]; then
ALERTMODE=""
else
ALERTMODE="-A $ALERTMODE"
fi
if [ "$USER"X = "X" ]; then
USER="snort"
fi
if [ "$GROUP"X = "X" ]; then
GROUP="snort"
fi
if [ "$BINARY_LOG"X = "1X" ]; then
BINARY_LOG="-b"
else
BINARY_LOG=""
fi
if [ "$CONF"X = "X" ]; then
CONF="-c /etc/snort/snort.conf"
else
CONF="-c $CONF"
fi
if [ "$INTERFACE"X = "X" ]; then
INTERFACE="-i eth0"
else
INTERFACE="-i $INTERFACE"
fi
if [ "$DUMP_APP"X = "1X" ]; then
DUMP_APP="-d"
else
DUMP_APP=""
fi
if [ "$NO_PACKET_LOG"X = "1X" ]; then
NO_PACKET_LOG="-N"
else
NO_PACKET_LOG=""
fi
if [ "$PRINT_INTERFACE"X = "1X" ]; then
PRINT_INTERFACE="-I"
else
PRINT_INTERFACE=""
fi
if [ "$PASS_FIRST"X = "1X" ]; then
PASS_FIRST="-o"
else
PASS_FIRST=""
fi
if [ "$LOGDIR"X = "X" ]; then
LOGDIR=/var/log/snort
Fi
# These are used by the 'stats' option
if [ "$SYSLOG"X = "X" ]; then
SYSLOG=/var/log/messages
fi
if [ "$SECS"X = "X" ]; then
SECS=5
fi
if [ ! "$BPFFILE"X = "X" ]; then
BPFFILE="-F $BPFFILE"
fi
######################################
# Now to the real heart of the matter:
# See how we were called.
case "$1" in
start)
echo -n "Starting snort: "
cd $LOGDIR
if [ "$INTERFACE" = "-i ALL" ]; then
for i in `cat /proc/net/dev|grep eth|awk -F ":" '{ print $1; }'`
do
mkdir -p "$LOGDIR/$i"
chown -R $USER:$GROUP $LOGDIR
daemon /usr/sbin/snort $ALERTMODE $BINARY_LOG $NO_PACKET_LOG $DUMP_APP -D $PRINT_INTERFACE -i $i -u $USER -g $GROUP $CONF -l $LOGDIR/$i $PASS_FIRST $BPFFILE $BPF
done
else
# check if more than one interface is given
if [ `echo $INTERFACE|wc -w` -gt 2 ]; then
for i in `echo $INTERFACE | sed s/"-i "//`
do
mkdir -p "$LOGDIR/$i"
chown -R $USER:$GROUP $LOGDIR
daemon /usr/sbin/snort $ALERTMODE $BINARY_LOG $NO_PACKET_LOG $DUMP_APP -D $PRINT_INTERFACE -i $i -u $USER -g $GROUP $CONF -l $LOGDIR/$i $PASS_FIRST $BPFFILE $BPF
done
else
# Run with a single interface (default)
daemon /usr/sbin/snort $ALERTMODE $BINARY_LOG $NO_PACKET_LOG $DUMP_APP -D $PRINT_INTERFACE $INTERFACE -u $USER -g $GROUP $CONF -l $LOGDIR $PASS_FIRST $BPFFILE $BPF
fi
fi
touch /var/lock/subsys/snort
echo
;;
stop)
echo -n "Stopping snort: "
killproc snort
rm -f /var/lock/subsys/snort
echo
;;
reload)
echo "Sorry, not implemented yet"
;;
restart)
$0 stop
$0 start
;;
condrestart)
[ -e /var/lock/subsys/snort ] && $0 restart
;;
status)
status snort
;;
stats)
TC=125 # Trailing context to grep
SNORTNAME='snort' # Process name to look for
if [ ! -x "/sbin/pidof" ]; then
echo "/sbin/pidof not present, sorry, I cannot go on like this!"
exit 1
fi
#Grab Snort's PID
PID=`pidof -o $$ -o $PPID -o %PPID -x ${SNORTNAME}`
if [ ! -n "$PID" ]; then # if we got no PID then:
echo "No PID found: ${SNORTNAME} must not running."
exit 2
fi
echo ""
echo "*******"
echo "WARNING: This feature is EXPERIMENTAL - please report errors!"
echo "*******"
echo ""
echo "You can also run: $0 stats [long | opt]"
echo ""
echo "Dumping ${SNORTNAME}'s ($PID) statistics"
echo "please wait..."
# Get the date and tell Snort to dump stats as close together in
# time as possible--not 100%, but it seems to work.
startdate=`date '+%b %e %H:%M:%S'`
# This causes the stats to be dumped to syslog
kill -USR1 $PID
# Sleep for $SECS secs to give syslog a chance to catch up
# May need to be adjusted for slow/busy systems
sleep $SECS
if [ "$2" = "long" ]; then # Long format
egrep -B 3 -A $TC "^$startdate .* snort.*: ={79}" $SYSLOG | \
grep snort.*:
elif [ "$2" = "opt" ]; then # OPTimize format
# Just show stuff useful for optimizing Snort
egrep -B 3 -A $TC "^$startdate .* snort.*: ={79}" $SYSLOG | \
egrep "snort.*: Snort analyzed |snort.*: dropping|emory .aults:"
else # Default format
egrep -B 3 -A $TC "^$startdate .* snort.*: ={79}" $SYSLOG | \
grep snort.*: | cut -d: -f4-
fi
;;
*)
echo "Usage: $0 {start|stop|reload|restart|condrestart|status|stats (long|opt)}"
exit 2
esac
exit 0
Code:
vi /usr/local/etc/barnyard2
Code:
#-------------------------------------------------------------
# Barnyard2 configuration file
#
# http://www.securixlive.com/barnyard2
#
# Contact: <a href="mailto:dev@securixlive.com">dev@securixlive.com</a>
#-------------------------------------------------------------
#
# This file contains a sample barnyard2 configuration.
# You can take the following steps to create your own custom configuration:
#
# 1) Configure the variable declarations
# 2) Setup the input plugins
# 3) Setup the output plugins
#
# Step 1: configure the variable declarations
#
# in order to keep from having a commandline that uses every letter in the
# alphabet most configuration options are set here.
# use UTC for timestamps
#
#config utc
# set the appropriate paths to the file(s) your Snort process is using.
#
config reference_file: /etc/snort/reference.config
config classification_file: /etc/snort/classification.config
config gen_file: /etc/snort/gen-msg.map
config sid_file: /etc/snort/sid-msg.map
# define dedicated references similar to that of snort.
#
#config reference: mybugs http://www.mybugs.com/?s=
# define explicit classifications similar to that of snort.
#
#config classification: shortname, short description, priority
# set the directory for any output logging
#
#config logdir: /tmp
# to ensure that any plugins requiring some level of uniqueness in their output
# the alert_with_interface_name, interface and hostname directives are provided.
# An example of usage would be to configure them to the values of the associated
# snort process whose unified files you are reading.
#
# Example:
# For a snort process as follows:
# snort -i eth0 -c /etc/snort.conf
#
# Typical options would be:
# config hostname: thor
# config interface: eth0
# config alert_with_interface_name
#
config hostname: localhost
config interface: eth0
config alert_with_interface_name
# enable printing of the interface name when alerting.
#
#config alert_with_interface_name
# at times snort will alert on a packet within a stream and dump that stream to
# the unified output. barnyard2 can generate output on each packet of that
# stream or the first packet only.
#
#config alert_on_each_packet_in_stream
# enable daemon mode
#
#config daemon
# make barnyard2 process chroot to directory after initialisation.
#
#config chroot: /var/spool/barnyard2
# specifiy the group or GID for barnyard2 to run as after initialisation.
#
#config set_gid: 999
# specifiy the user or UID for barnyard2 to run as after initialisation.
#
#config set_uid: 999
# specify the directory for the barnyard2 PID file.
#
#config pidpath: /var/run/by2.pid
# enable decoding of the data link (or second level headers).
#
#config decode_data_link
# dump the application data
#
#config dump_payload
# dump the application data as chars only
#
#config dump_chars_only
# enable verbose dumping of payload information in log style output plugins.
#
#config dump_payload_verbose
# enable obfuscation of logged IP addresses.
#
#config obfuscate
# enable the year being shown in timestamps
#
#config show_year
# set the umask for all files created by the barnyard2 process (eg. log files).
#
#config umask: 066
# enable verbose logging
#
#config verbose
# quiet down some of the output
#
#config quiet
# define the full waldo filepath.
#
config waldo_file: /var/log/snort/barnyard2.waldo
# specificy the maximum length of the MPLS label chain
#
#config max_mpls_labelchain_len: 64
# specify the protocol (ie ipv4, ipv6, ethernet) that is encapsulated by MPLS.
#
#config mpls_payload_type: ipv4
# set the reference network or homenet which is predominantly used by the
# log_ascii plugin.
#
#config reference_net: 192.168.0.0/24
#
# CONTINOUS MODE
#
# set the archive directory for use with continous mode
#
#config archivedir: /tmp
# when in operating in continous mode, only process new records and ignore any
# existing unified files
#
#config process_new_records_only
# Step 2: setup the input plugins
#
# this is not hard, only unified2 is supported ;)
input unified2
# Step 3: setup the output plugins
# alert_cef
#-----------------------------
#
# Purpose:
# This output module provides the abilty to output alert information to a
# remote network host as well as the local host using the open standard
# Common Event Format (CEF).
#
# Arguments: host=hostname[:port], severity facility
# arguments should be comma delimited.
# host - specify a remote hostname or IP with optional port number
# this is only specific to WIN32 (and is not yet fully supported)
# severity - as defined in RFC 3164 (eg. LOG_WARN, LOG_INFO)
# facility - as defined in RFC 3164 (eg. LOG_AUTH, LOG_LOCAL0)
#
# Examples:
# output alert_cef
# output alert_cef: host=192.168.10.1
# output alert_cef: host=sysserver.com:1001
# output alert_cef: LOG_AUTH LOG_INFO
#
# alert_bro
#-----------------------------
#
# Purpose: Send alerts to a Bro-IDS instance.
#
# Arguments: hostname:port
#
# Examples:
# output alert_bro: 127.0.0.1:47757
# alert_fast
#-----------------------------
# Purpose: Converts data to an approximation of Snort's "fast alert" mode.
#
# Arguments: file <file>, stdout
# arguments should be comma delimited.
# file - specifiy alert file
# stdout - no alert file, just print to screen
#
# Examples:
# output alert_fast
# output alert_fast: stdout
#
output alert_fast: stdout
# prelude: log to the Prelude Hybrid IDS system
# ---------------------------------------------
#
# Purpose:
# This output module provides logging to the Prelude Hybrid IDS system
#
# Arguments: profile=snort-profile
# snort-profile - name of the Prelude profile to use (default is snort).
#
# Snort priority to IDMEF severity mappings:
# high < medium < low < info
#
# These are the default mapped from classification.config:
# info = 4
# low = 3
# medium = 2
# high = anything below medium
#
# Examples:
# output alert_prelude
# output alert_prelude: profile=snort-profile-name
#
# alert_syslog
#-----------------------------
#
# Purpose:
# This output module provides the abilty to output alert information to a
# remote network host as well as the local host.
#
# Arguments: host=hostname[:port], severity facility
# arguments should be comma delimited.
# host - specify a remote hostname or IP with optional port number
# this is only specific to WIN32 (and is not yet fully supported)
# severity - as defined in RFC 3164 (eg. LOG_WARN, LOG_INFO)
# facility - as defined in RFC 3164 (eg. LOG_AUTH, LOG_LOCAL0)
#
# Examples:
# output alert_syslog
# output alert_syslog: host=192.168.10.1
# output alert_syslog: host=sysserver.com:1001
# output alert_syslog: LOG_AUTH LOG_INFO
#
# log_ascii
#-----------------------------
#
# Purpose: This output module provides the default packet logging funtionality
#
# Arguments: None.
#
# Examples:
# output log_ascii
#
# log_tcpdump
# -------------------------------------------------
#
# Purpose
# This output module logs packets in binary tcpdump format
#
# Arguments:
# The only argument is the output file name.
#
# Examples:
# output log_tcpdump: tcpdump.log
#
# sguil
#-----------------------------
#
# Purpose: This output module provides logging ability for the sguil interface
# See doc/README.sguil
#
# Arguments: agent_port <port>, sensor_name <name>
# arguments should be comma delimited.
# agent_port - explicitly set the sguil agent listening port
# (default: 7736)
# sensor_name - explicitly set the sensor name
# (default: machine hostname)
#
# Examples:
# output sguil
# output sguil: agent_port=7000
# output sguil: sensor_name=argyle
# output sguil: agent_port=7000, sensor_name=argyle
#
# database: log to a variety of databases
# ---------------------------------------
#
# Purpose: This output module provides logging ability to a variety of databases
# See doc/README.database for additional information.
#
# Examples:
# output database: log, mysql, user=root password=test dbname=db host=localhost
output database: log, mysql, user=snort password=123456 dbname=snort host=localhost
# output database: alert, postgresql, user=snort dbname=snort
# output database: log, odbc, user=snort dbname=snort
# output database: log, mssql, dbname=snort user=snort password=test
# output database: log, oracle, dbname=snort user=snort password=test
Code:
vi /etc/snort/rules/local.rules
Có các rule tự tạo
Code:
#-------------
# LOCAL RULES
#-------------
alert tcp any any -> 192.168.1.2/24 any (msg:"Testing ScanPort 80"; sid:10000 01;)
alert tcp 192.168.1.3/24 any -> 192.168.1.2/24 any (msg:"Testing ScanPort 22" ; sid:1000002;)
alert ip any any -> any any (msg:"IP Testing Rule"; sid:1000003;)
alert icmp any any -> any any (msg:"ICMP Testing Rule"; sid:1000004;)
alert tcp any any -> any any (msg:"TCP Testing Rule"; sid:1000005;)
alert udp any any -> any any (msg:"UDP Testing Rule"; sid:1000006;)
alert tcp 192.168.1.3/24 any -> any 80 (msg:"ScanPort 80"; sid:1000007;)
alert tcp 192.168.1.3/24 any -> any 22 (msg:"ScanPort 22"; sid:1000008;)sid:1000008;)
Kiêm tra hoạt động của banyard2 bằng câu lệnh
Code:
barnyard2 -c /etc/snort/barnyard2.conf -d /var/log/snort/ -f snort.log -w /var/log/snort/barnyard2.waldo
hoặc
barnyard2 -c /etc/snort/barnyard2.conf -f merged.log -d /var/log/snort
Thấy chạy ra nhiều nội dung nhưng đến dòng
Code:
Opened spool file '/var/log/snort//snort.log.1384864281'
Waiting for new data
Thì thấy đứng lại rất lâu, chắc đang chạy tiếp
Kiểm tra hoạt động của snort
Code:
snort -c /etc/snort/snort.conf -i eth0 -u snort -g snort
hoặc
snort -u snort -g snort -d -c /etc/snort/snort.conf
Thấy chạy nhưng đến dòng này
Code:
Commencing packet processing (pid=5633)
Thì thấy đứng rất lâu chắc nó đang chạy tiếp.
Code:
Thấy nội dung
Code:
total 19376
-rw-r--r--. 1 root root 11473353 Nov 19 04:29 alert
-rwxr-xr-x. 1 snort snort 2056 Nov 19 04:26 barnyard2.waldo
-rwxr-xr-x. 1 root root 0 Nov 18 00:47 snort.alert
-rwxr-xr-x. 1 root root 0 Nov 18 00:47 snort.log
-rw-------. 1 snort snort 10368 Nov 18 18:55 snort.log.1384829558
-rw-------. 1 snort snort 2511 Nov 18 19:01 snort.log.1384829740
-rw-------. 1 snort snort 412009 Nov 18 19:12 snort.log.1384830271
-rw-------. 1 snort snort 342686 Nov 18 19:24 snort.log.1384830766
-rw-------. 1 snort snort 264727 Nov 18 19:34 snort.log.1384831550
-rw-------. 1 snort snort 1048649 Nov 18 19:51 snort.log.1384832827
-rw-------. 1 snort snort 12114 Nov 18 20:03 snort.log.1384833256
-rw-------. 1 snort snort 37632 Nov 19 01:38 snort.log.1384853634
-rw-------. 1 snort snort 1825550 Nov 19 01:58 snort.log.1384853921
-rw-------. 1 snort snort 4365676 Nov 19 04:29 snort.log.1384855103
-rw-------. 1 snort snort 5922 Nov 19 04:25 snort.log.1384863836
-rw-------. 1 snort snort 2710 Nov 19 04:26 snort.log.1384863949
-rw-------. 1 root root 1300 Nov 19 04:29 snort.log.1384864116
Kiểm tra lại hoạt động của snort
Code:
./snort -T -i eth0 -u snort -g snort -c /etc/snort/snort.conf
Thấy chạy ra nhiều nội dung và kết thúc là
Code:
Snort successfully validated the configuration!
Snort exiting
Code:
Thấy hiển thị nội dung
Code:
snort 4062 0.3 0.9 400764 5016 ? Ssl 03:48 0:10 /usr/sbin/snort -A fast -b -d -D -i eth0 -u snort -g snort -c /etc/snort/snort.conf -l /var/log/snort
root 5383 0.0 1.1 14588 6108 ? Ss 04:23 0:00 barnyard2 -c /etc/snort/barnyard2.conf -f merged.log -d /var/log/snort -D
snort 5388 0.9 0.7 400704 3760 pts/0 Tl 04:23 0:10 snort -c /etc/snort/snort.conf -i eth0 -u snort -g snort
snort 5475 1.1 0.7 400480 3592 pts/0 Tl 04:25 0:10 snort -u snort -g snort -d -c /etc/snort/snort.conf
root 5545 0.0 2.0 28604 10576 pts/0 T 04:28 0:00 snort -dev -l /var/log/snort/
snort 5633 1.7 28.5 400764 145928 pts/0 Tl 04:31 0:10 snort -u snort -g snort -d -c /etc/snort/snort.conf
root 5657 2.3 1.2 14568 6560 pts/0 T 04:32 0:11 barnyard2 -c /etc/snort/barnyard2.conf -d /var/log/snort/ -f snort.log -w /var/log/snort/barnyard2.waldo
root 5748 3.3 1.2 14568 6576 pts/0 T 04:35 0:11 barnyard2 -c /etc/snort/barnyard2.conf -f merged.log -d /var/log/snort
root 5868 2.0 0.1 4356 724 pts/0 D+ 04:40 0:00 grep -i snort
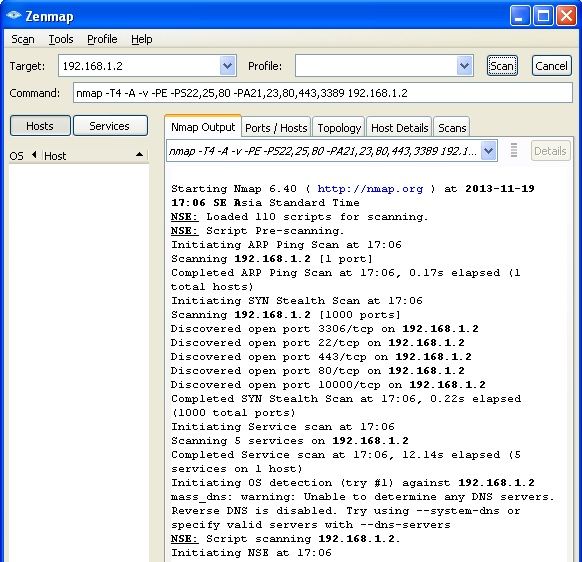
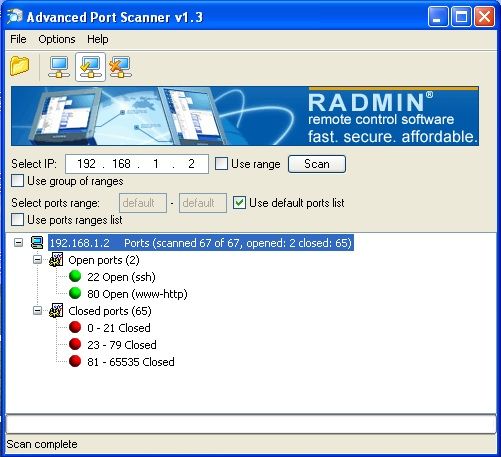
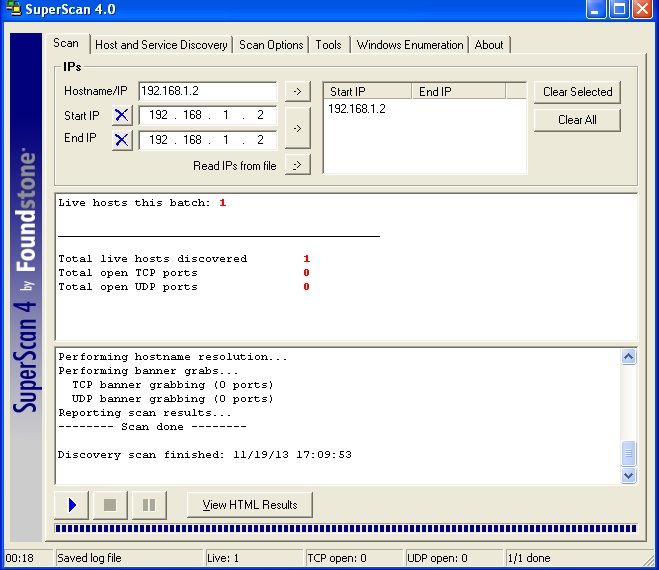
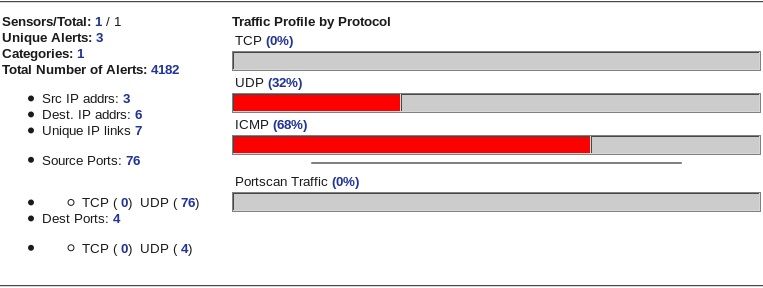
Vấn đề thứ 2 mình muốn hỏi là sao đã thực hiện scanport bằng nmap, advance port scan, superscan4 như hình dưới
Base không hiển thị portscan traffic hay TCP
![[digg] [digg]](/hvaonline/templates/viet/images/digg.gif)
![[delicious] [delicious]](/hvaonline/templates/viet/images/delicious.gif)
![[google] [google]](/hvaonline/templates/viet/images/google.gif)
![[yahoo] [yahoo]](/hvaonline/templates/viet/images/yahoo.gif)
![[technorati] [technorati]](/hvaonline/templates/viet/images/technorati.gif)
![[reddit] [reddit]](/hvaonline/templates/viet/images/reddit.gif)
![[stumbleupon] [stumbleupon]](/hvaonline/templates/viet/images/stumbleupon.gif)



![[Minus] [Minus]](/hvaonline/templates/viet/images/minus.gif)
![[Plus] [Plus]](/hvaonline/templates/viet/images/plus.gif)